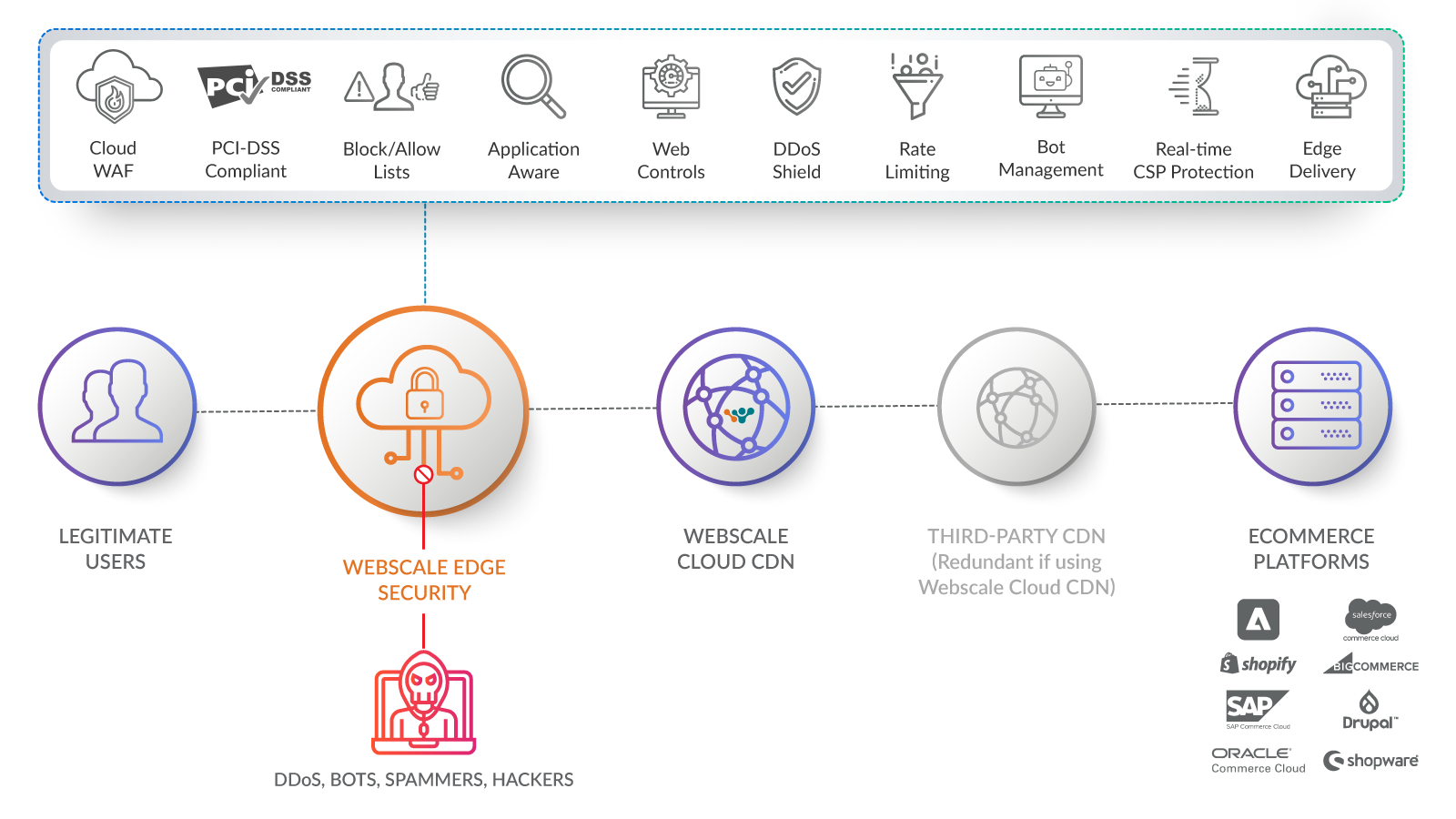
Webscale Security
Manage and mitigate complex threats to protect revenue and reputation
The Webscale Security Suite leverages analytics and automation to deliver proactive monitoring, detection, diagnosis and alerting to protect storefronts from complex threats. Deployed at the edge, and all the way to the backend, the Webscale Security Suite is the only protection your storefront will ever need.
Every merchant will face a security threat
Every year ecommerce merchants, and their customers lose billions of dollars due to credit card fraud, carding attacks, bad bots, malicious injections, and other attacks that compromise the integrity of an online transaction. Can you survive a security breach? If you do, will your customers return?
Key Capabilities

360-degree Continuous Protection
Enterprise-grade ecommerce security from the edge to the origin
Modern commerce has many touch points, leaving the front and back ends equally vulnerable. Are you trusting your brand reputation to a simple WAF (web application firewall) – a “front-door” security solution that leaves the “back-doors” open?
- Webscale leverages automation and analytics to ensure total protection from the origin to the edge
- Proactive monitoring, detection and mitigation of the most dangerous attacks, including form jacking (Magecart), bots & scrapers, access breaches, DDoS attacks, and injections (SQL and XSS)
Defend Against Account Takeovers
Detect repeated failed login attempts in real-time
Social engineering attacks, like phishing, are commonly used to extract ecommerce account information from unsuspecting shoppers, and are often used to conduct credential stuffing attacks
- Webscale’s real-time Traffic Viewer provides deep visibility into login pages, tracking both successful and failed logins, detecting brute force attacks
- Rate Limiting shuts down, or restricts access, to login pages


Avoid Serving Bot Traffic
Deliver a flawless user experience, for real users
Bots can represent more than 50% of ecommerce site traffic. Bad bots can consume cloud capacity, scrape content, and cause slow downs that impact the user experience for real customers.
- Rate Limiting and Web Controls allow merchants to block threats, limit their requests, and provide access to valid users only
- Webscale Bot Manager identifies legitimate bots (Google, Bing) using pre-configured Address Sets, and serves them from Dynamic Site Cache freeing up infrastructure
“We’ve been very impressed with the security and support offered by Webscale. It’s far in advance of anything we have received before.”
Going Beyond Detection
Quick mitigation, and long term prevention
Does your security solution provider stop with detection? Many leave remediation to the merchant or the developer, leading to a delay in both preventing the breach, or containing the impact of the attack.
- Webscale’s DevSecOps team works alongside developer and admin teams to not only detect, but mitigate security threats
- Perform quick mitigation with Web Controls, and advanced features like CSP (content security policy) Protection, DDoS Shield and App Shield


100% Compliance
Strengthen customer trust and loyalty
Almost 60% of small to medium-sized ecommerce businesses don’t survive a cyber attack due to the loss of customer trust and brand reputation. With Webscale, you can protect your customers’ personal and financial data from threats, without making any changes to your application.
- Webscale Malware Scanners are on 24-7, conducting monitoring and alerting in real-time
- PCI-DSS Level 1 compliant; SOC2 Type II certified; HIPAA compliant

“Webscale pays for itself – the value we get from their security solution and 24×7 support is unquestionable.”
How Does It Work?
Have a question? Chat or send us a message below
Customer Testimonials
FAQs
Will Webscale Security work on my site or native app?
Yes, Webscale Security will work on your ecommerce website and native application.
My hosting provider/hosted ecommerce platform/CDN/WAF offers security. Why do I need extra security from Webscale?
Webscale software plans come with pre-bundled security features.
Most ecommerce businesses rely on their public cloud service provider’s security and/or sign up for a WAF (Web Application Firewall), which is not suitable as a stand-alone security solution. Some CDNs come with an inbuilt WAF and/or DDoS protection as a feature but again, they are limited in scope with regards to the range of threats they can defend against. Modern commerce is being targeted by complex and evolving threats that demand enterprise-grade security. With omnichannel commerce, the perimeter is expanding with numerous touchpoints and third party integrations, all opening up new and unknown vulnerabilities.
Webscale’s security stack has been purpose-built for ecommerce and leverages AL/ML-led automation and deep analytics to protect checkouts and storefronts from sophisticated attacks: form jacking (Magecart), bots & scrapers, access breaches, DDoS attacks, broken access control, cryptographic failures, injection (SQL and XSS) and server-side request forgery (SSRF).
How do I choose my plan?
The comparison chart on the Pricing page provides a simple breakdown of our plans by feature, so you can choose a plan that best addresses your business needs. If you’d like some help, reach out to us here
How is Webscale Security deployed? How long will it take?
There are multiple ways we can engage with you to deploy Webscale Security.
-
For Webscale hosted merchants, Webscale Security is deployed along with your environment and takes no time at all.
-
For merchants on hosted commerce clouds, deploying Webscale Security, involves simply pointing their website’s DNS to the Webscale proxy hostname and then configuring using their origin IP.
-
For new merchants moving to Webscale, the timeline depends on the migration schedule.
Can you integrate with my existing CDN and/or WAF?
Yes. Webscale Security can be deployed at the edge, alongside any pre-existing solution.
Will the deployment impact the performance of my site/app?
Not at all.
Is Support included in your plans?
All Webscale software plans come with the Webscale Silver Support package. In addition to that, Webscale offers two more support packages – Gold and Platinum – for merchants requiring various levels of support from faster troubleshooting and advanced infrastructure monitoring to dedicated assistance in the day-to-day management and optimization of their storefronts. Webscale also offers several Add-on Services, including DevOps Support, Code & Infrastructure Reviews, Application Load Testing, and Cloud Hosting.
What is your level of compliance?
Webscale is PCI-DSS Level 1, SOC2 Type II and HIPAA compliant.








