Massive global events like Black Friday and Cyber Monday trigger pure online shopping mayhem. According to Forbes, online sales during Black Friday and Cyber Monday amounted to US$12.8 billion in 2016, depicting a 15.2% spike over the previous year. What’s more, almost 40% of these sales happened on mobile devices. Just one year later, shoppers broke their own record, spending $1 million per minute at the peak of the holiday.
Holiday season or hacking season?
It isn’t just the shoppers (and the online stores) who look forward to the holiday season. With more consumers buying online than ever before and e-commerce spending running into the billions, hackers and cybercriminals are being presented with an opportunity too good to miss.
Here are seven of the most common ways a cyber-attack can occur:
- Account takeovers: This is when hackers (humans or bots) get access to customer account credentials (usernames and passwords), resulting in a severe breach of confidential information, possibly including credit card details. This exposes the merchant to multiple threats such as identity theft, financial fraud, and inevitably leads to a loss of customer confidence.
- Hijacked gift cards: Gift cards – especially e-gift cards – are very popular during the holiday season, especially if you suspect Grandpa is getting a little tired of socks! They are a common target for hackers, who try to guess the the correct pin (which consist of three to four digits, at most) and use the unlocked card value without having to take over an account.
- Distributed denial of service (DDoS) attacks: A DDoS attack is where a hacker makes an online resource unavailable to its users by disrupting connectivity, either temporarily or indefinitely. The attack is perpetrated via a flood of traffic to the server from multiple disparate sources, such as botnets, making it virtually impossible to stop by simply blocking a single source.
- Phishing: Phishing is an attempt to fraudulently obtain sensitive information such as usernames, passwords, and credit card details by e-mailing or instant-messaging users. Attackers attempt to lure consumers to visit fake websites, that look identical to their legitimate counterparts, and ask for them to enter personal information, which can then be used to take over accounts, or sold to the highest bidder on the dark web. Phishing e-mails may also lure victims to malware-infected websites.
- Malware: This involves the deployment of infected software with the intent of stealing guarded business information, such as customer and financial information. It can even be used to disrupt operations, and can take several forms, including viruses, worms, Trojan horses, ransomware, and spyware. This can be very disruptive since the actual vulnerability may be discovered a long time after the infrastructure and customer information have already been used and exploited.
- Inventory buyout: The holiday season inevitably sees hot items, such as popular toys or consumer gadgets, sell out in days or even minutes. Hackers track these favorites and buy them out with the intention of selling them on a secondary site at higher price points.
- Content and price scraping: This involves competitors acquiring a complete copy of your available business information, including inventory, pricing, and other sensitive data – in a bid to acquire a competitive edge in the market. It can undermine a company’s competitive standing and destroy market advantage.
How can you protect your storefront?
If you’re an e-commerce store owner, cyber-attacks can cause massive and lasting damage in the form of brand dilution. There is also the obvious and immediate loss of user loyalty and revenue, if the user is directly affected by the attack. All these factors lead to an inevitable user churn, which in most cases is irreversible. Would you return to an online store that had allowed your personal data to be stolen? How about if that data has then been used to impact your credit score?
To make matters worse, cyber-attacks are unpredictable. Though their probability increases during peak seasons, there is literally no way to know when an attack will take place. In addition, cyber-attacks keep changing – both in terms of strategy and execution.
Finally, security attacks are often not simple. Attackers can be very sophisticated in their means to exploit a storefront, often doing so in an undetected manner for long periods of time.
So how do you avert a malicious attack? Here’s an initial list of things to do:
- Learn about common attacks, analyze traffic, and discover suspect patterns, then challenge or block these patterns
- Detect potential attacks before they impact your application layer and database (where your storefront and customer data reside)
- Analyze prior and attempted attacks and classify perpetrators as humans or bots
- Be proactive in keeping out known bad bots and IPs
- Protect customer accounts by insisting on strong and unique usernames and passwords, and ones that change often. Ensure administrators have multiple factors of authentication to access the storefront backend.
- Ensure compliance with robust IT security best practices. If you’re not PCI-DSS compliant, then you need to act fast!
The good news is, there are solutions available in the market to help you with these. These come in the form of content delivery networks (CDNs) and web application firewalls (WAFs). The bad news is, most of them only partially address the issue. They only take care of security at the edge, where user traffic commences its journey to the origin, but not the application infrastructure itself, which is a dangerous security posture to assume given the rate at which application layer attacks are increasing.
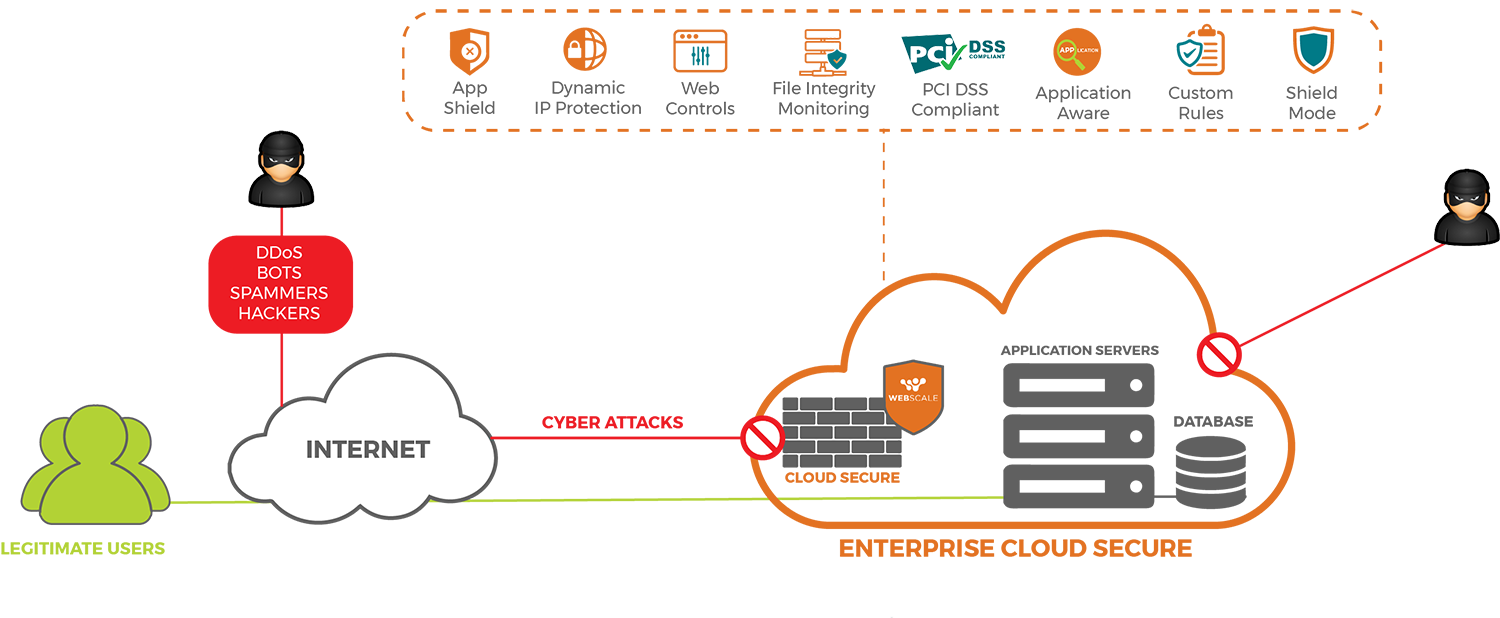
What e-commerce storefronts need is a holistic solution – one that protects core infrastructure just as much as traffic at the edge; identifies patterns and behaviors to provide deep insights into potential threats; is compliant with all necessary regulations; and provides round-the-clock security, access, and uptime. Something like Enterprise Cloud Secure, Webscale’s 360° protection solution for your web application infrastructure. Check out this datasheet if you’d like to learn more, or reach out to us at sales@webscalenetworks.com if you’d like to speak with one of our e-commerce specialists.